Sponsored by Exabeam
Sponsored by Abnormal Security
CISO Guide to Ransomware: How It Starts Via Email & How to Prevent It
Sponsored by Immersive Labs
eBook: 3 Steps to Ultimate Cyber Resilience
Sponsored by Secureworks
2021 State of the Threat: A Year in Review
Sponsored by Proofpoint
The Modern CISO’s Framework for Identifying, Classifying and Stopping Email Fraud
Sponsored by Abnormal Security
The Evolution of Ransomware: Victims, Threat Actors, and What to Expect in 2022
Sponsored by Vectra AI
Ransomware: 'Because It's Not a Matter of If, But When'
Sponsored by CSI
The Dangerous Intersection Between OFAC And Ransomware
Sponsored by Hitachi ID
An IAM & PAM Industry Guide to Ransomware: A Winning Defense with Zero Trust
Sponsored by Dell Technologies & DXC Technology
How to Protect Against the Impacts of a Ransomware Attack
Sponsored by Veritas
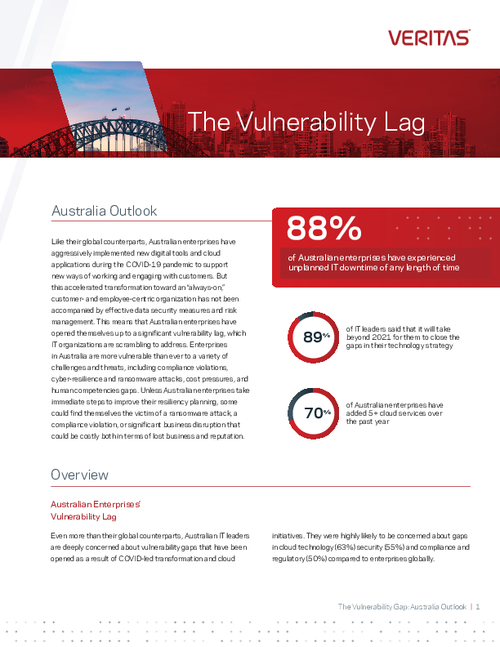
The Vulnerability Lag - Australia
Sponsored by Veritas