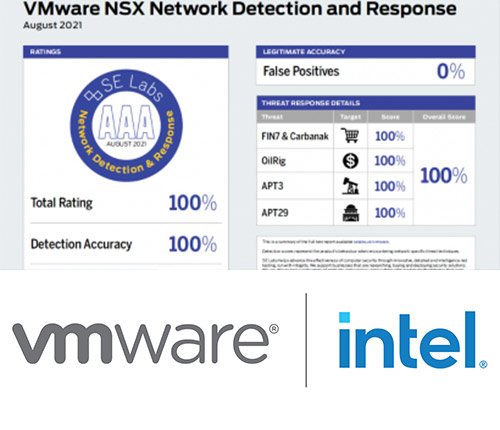
Sponsored by VMware
Lateral Movement in the Real World: A Quantitative Analysis
Sponsored by CounterCraft
Deception-Powered Threat Intelligence for the Retail Industry
Sponsored by Palo Alto Networks
Five Things to Consider Before Embarking on a SASE Project
Sponsored by Microsoft and Check Point
ZTNA Buyer's Guide
Sponsored by Abnormal Security
2022 Email Security Trends Survey Report
Sponsored by CrowdStrike
Adapt or Die: XDR Is On A Collision Course With SIEM And SOAR
Sponsored by Verizon
A CISO’s Guide to Selecting a Managed Detection and Response Partner
Sponsored by Palo Alto Networks
Advanced Threats Require Advanced Defenses
Sponsored by Vectra
Explore Vectra's Threat Detection and Response
Sponsored by Rapid7