Sponsored by Rapid7
Sponsored by ServiceNow
5 Stages of Security Automation Maturity: How Do You Compare?
Sponsored by Kroll
The State of Incident Response 2021: It’s Time for a Confidence Boost
Sponsored by Cyrebro
Seven Steps to Effective Incident Response
Sponsored by Gigamon
2020 Gartner Market Guide for Network Detection and Response
Sponsored by 1Password
How to Avoid a Data Breach
Sponsored by Vera, a Helpsystems Company
Dynamic Data Protection for Financial Services
Sponsored by ServiceNow
Forrester TEI ServiceNow Security Operations Solutions
Sponsored by Graylog
4 Steps To Planning A Successful Data Breach Incident Response
Sponsored by Open Raven
Finding & Eliminating Sensitive Data in Logs
Sponsored by Team Cymru
What Elite Threat Hunters See That Others Miss
Sponsored by Team Cymru
Case Study: Leading Financial Institutions
Sponsored by Team Cymru
Forrester Total Economic Impact Whitepaper
Sponsored by Fortinet
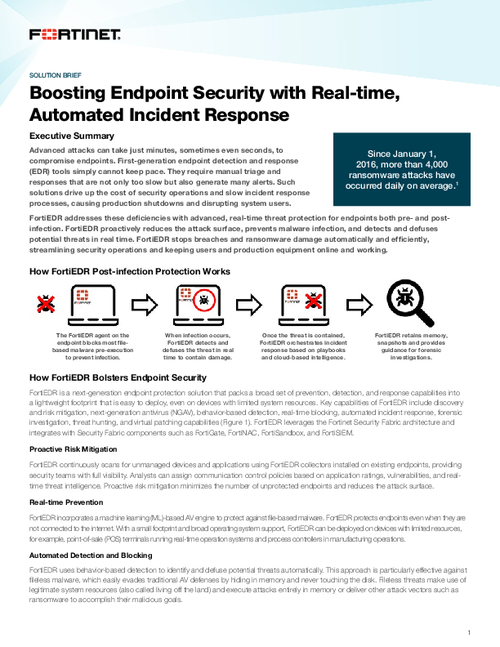
Boosting Endpoint Security with Real-time, Automated Incident Response
Sponsored by Fortinet