Sponsored by Red Canary
Sponsored by Red Canary
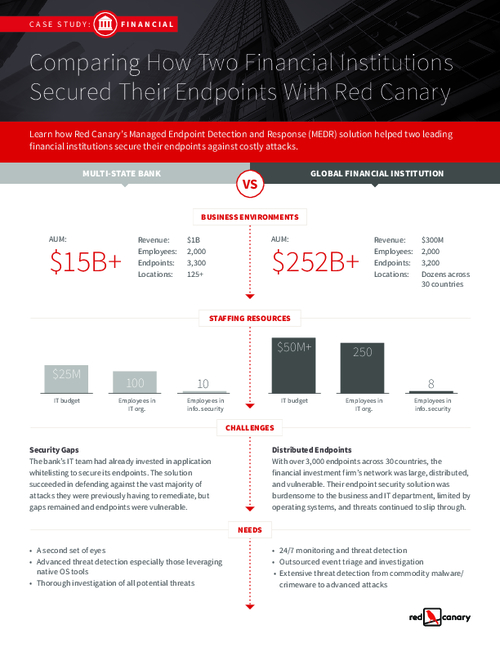
Case Study: How Two Financial Institutions Secured Their Endpoints
Sponsored by Red Canary
Case Study: How an Investment Firm Uses Multiple MSSPs
Sponsored by ValiMail
The DMARC Implementation Challenge
Sponsored by ValiMail
Email Authentication: The Big Picture
Sponsored by ValiMail
96% of .Gov Domains Are Not Ready for DHS Deadlines
Sponsored by Illumio
Micro-Segmentation: Fast Becoming a Foundational Layer of Security Architecture
Sponsored by iovation
10 Multi-Factor Authentication (MFA) Platform Buying Criteria
Sponsored by IBM
Empower Security Analysts With Actionable Data
Sponsored by Trend Micro
Report: Security Trends in 2018
Sponsored by Trend Micro
Report: Security Predictions for 2018
Sponsored by IBM
Identifying New Mobile Banking Fraud Patterns
Sponsored by Trend Micro
What SMBs Can Do to Handle BYOD Concerns
Sponsored by Trend Micro