3rd Party Risk Management , Business Continuity Management / Disaster Recovery , Critical Infrastructure Security
Ransomware: Average Ransom Payment Stays Steady at $140,000
Big Game Hunting Is Out and 'Mid Game Hunting' Is In, Coveware Warns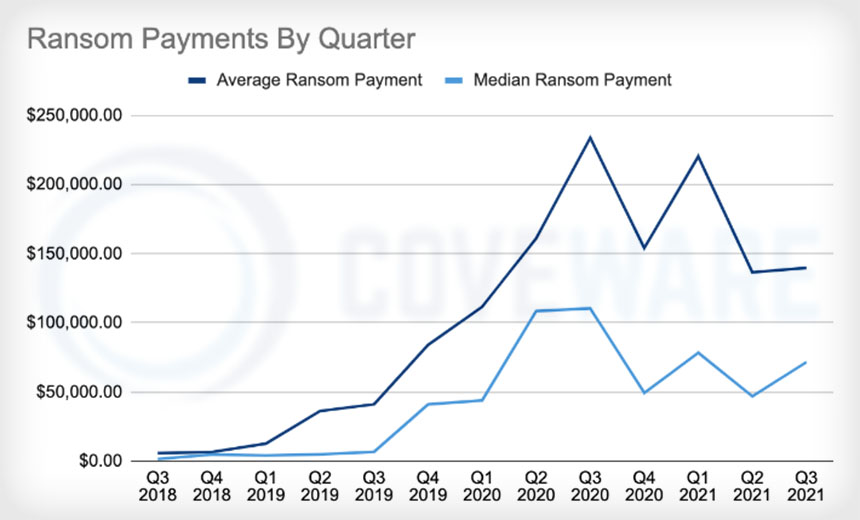
When a business, government agency or any other organization gets hit by ransomware and opts to pay a ransom to its attacker in exchange for a decryption key or some other promise, on average it pays $140,000.
See Also: The State of Organizations' Security Posture as of Q1 2018
So says ransomware incident response firm Coveware, based on thousands of incidents it investigated from July through August.
In a new report detailing Q3 trends, Coveware says that the average ransom payment remained largely steady, compared to Q2, while the median increased by more than 50%.
This shift, it says, started after a number of high-profile attacks that began in May, including DarkSide disrupting U.S.-based Colonial Pipeline, causing consumers to panic-buy fuel. Not long after, REvil - aka Sodinokibi - attacked meat processing giant JBS, and over the July Fourth holiday weekend, it hit remote management software firm Kaseya's software, used by managed service providers, to encrypt and hold to ransom systems used by more than 1,500 of those MSPs' customers.
The attacks sparked a furious political response from the Biden administration and other governments, galvanizing international efforts to target ransomware attackers via law enforcement means, disrupt cryptocurrency flows to eat away at profits, and focus on improving the cybersecurity resilience of domestic businesses. The White House has also been increasing diplomatic pressure on Moscow to crack down on cybercriminals operating from inside Russia's borders.
Seemingly in response to the fallout, DarkSide ceased operations, rebranding as BlackMatter. REvil went offline in July for unexplained reasons, before resurfacing in September. The same month, security firm Bitdefender received from law enforcement officials the keys that enabled it to build and release a free decryptor for almost all REvil infections dating from July and before. This month, REvil's infrastructure went offline again, with an administrator claiming operators pulled the plug after someone hijacked REvil's Tor-based data leak and payment portal sites.
'Mid Game Hunting'
Meanwhile, the ransomware attack landscape has continued to shift in other ways too. "Ever since the pipeline attacks this spring, we have seen statistical evidence and intelligence showing that ransomware actors are trying to avoid larger targets that may evoke a national political or law enforcement response," Coveware says. "This shift from 'big game hunting' to 'mid game hunting' is personified in both the ransom amount statistics but also the victim size demographics from the quarter."
Indeed, based on its Q3 investigations, Coveware says small and midsize professional services firms - and especially law firms and financial services firms - appear to be most at risk from ransomware attacks, due to their lack of information security preparedness, seemingly because they believe they're too small to be targeted.
But ransomware-wielding attackers seeking illicit profits generally do not target any particular organization, but rather look more broadly for poorly prepared sectors that offer maximum opportunity for returns, which has made small and midsize professional services firms "a lightning rod for attacks," Coveware says.
At the same time, while efforts being brought to bear to disrupt ransomware are welcome, so far they do not appear to be having any discernable effect, Coveware says.
"Ransomware industry actors face little to no risk when carrying out attacks," it says. "There is effectively zero downside to becoming a ransomware affiliate and the extortion economy is attracting new entrants every day. Until the economics are disrupted and the risks start to outweigh the rewards, the problem will persist and grow."
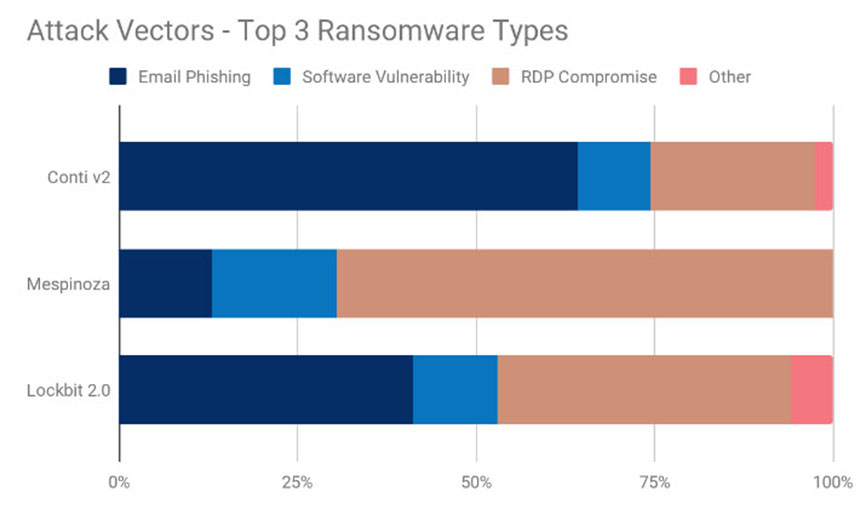
Most-Seen Strains: Conti, Mespinoza
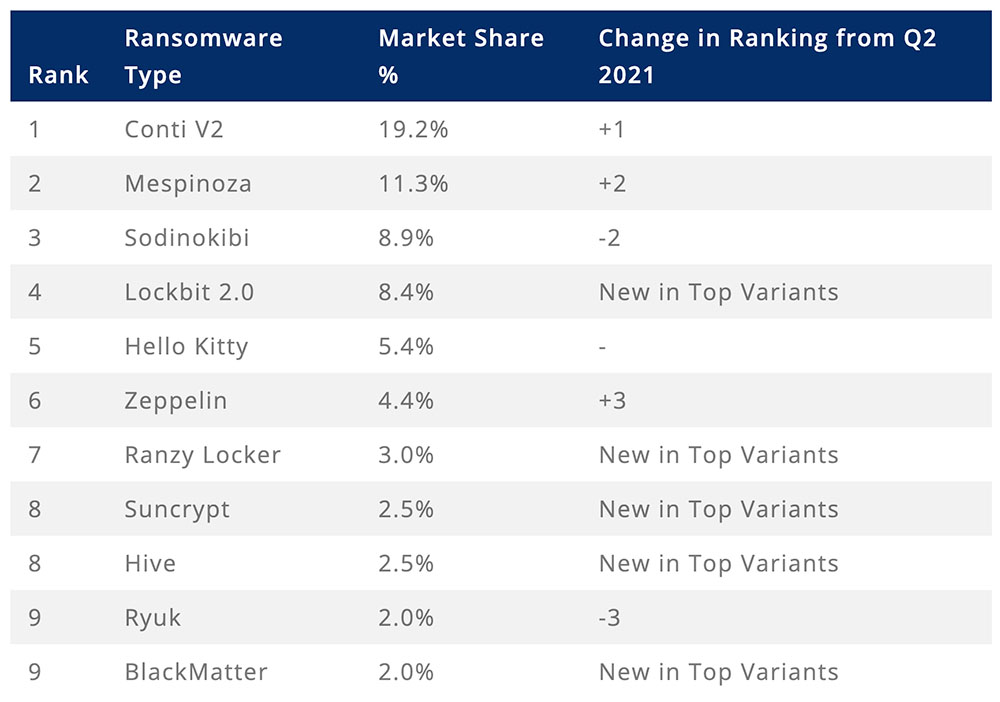
The top ransomware strains seen by the firm in Q3 were Conti, Mespinoza, Sodinokibi - aka REvil, LockBit 2.0 and Hello Kitty. All are ransomware-as-a-service operations, meaning a core group of developers and administrators maintains the malware and any dedicated data leak site and recruits affiliates to infect victims. Whenever a victim pays, the responsible affiliate and ransomware operator are meant to share in the profits.
Most Common Ransomware Variants in Q3 2021
But REvil, at least, recently got caught out for having included a backdoor in its malware, allowing administrators to steal affiliates' cuts (see: Ransomware Soap Opera Continues With REvil's Latest Outage).
Top Tactics and Threats
In terms of tactics, techniques and procedures, or TTPs, being wielded by attackers, 83% of all ransomware attacks in Q3 - up from 80% in Q2 - included a threat to leak stolen data. But security experts continue to warn that attackers often lie about having stolen data that has any value (see: Ransomware: No Decline in Victims Posted to Data Leak Sites).
In addition, paying a ransom in whole or part for a promise from attackers to delete stolen data comes with no guarantees. Security experts warn that businesses that do pay a ransom will often face an additional monetary demand from the same set of attackers or get hit again by the same operation, or a different one, looking to capitalize on the victim's propensity to pay.
Advice for Defenders
How can organizations better defend themselves against ransomware, based on recent attack trends?
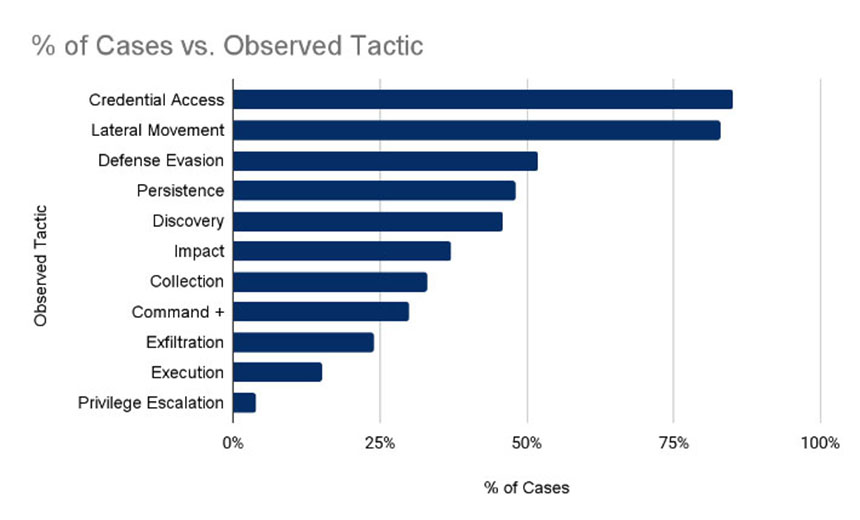
"Securing a large enterprise network is a never-ending task," Coveware says. "However, the rate at which ransomware threat actors reuse TTPs presents an opportunity for defenders to select areas of weakness that can be addressed quickly and cost effectively," keeping in mind that successful attacks always require chaining together multiple tactics.
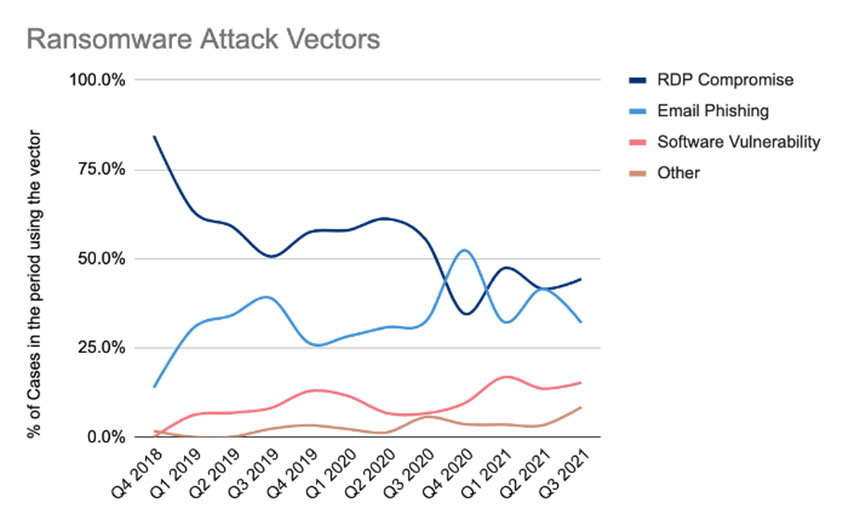
Notably, initial access trends have remained largely steady in recent years: Poorly secured remote desktop access - aka RDP - and phishing attacks remain the top two tactics used by ransomware-wielding criminals to gain initial access to a victim's network. But Coveware says more attacks than before are also targeting known vulnerabilities in software.
"By identifying opportunities along the kill chain to halt these attacks, enterprises can opportunistically reduce risk," Coveware says.




















