Cybercrime as-a-service , Endpoint Security , Fraud Management & Cybercrime
Ransomware Attacks Hitting Vulnerable MySQL Servers
Researchers: Attackers Also Selling Access to Over 250,000 Stolen Databases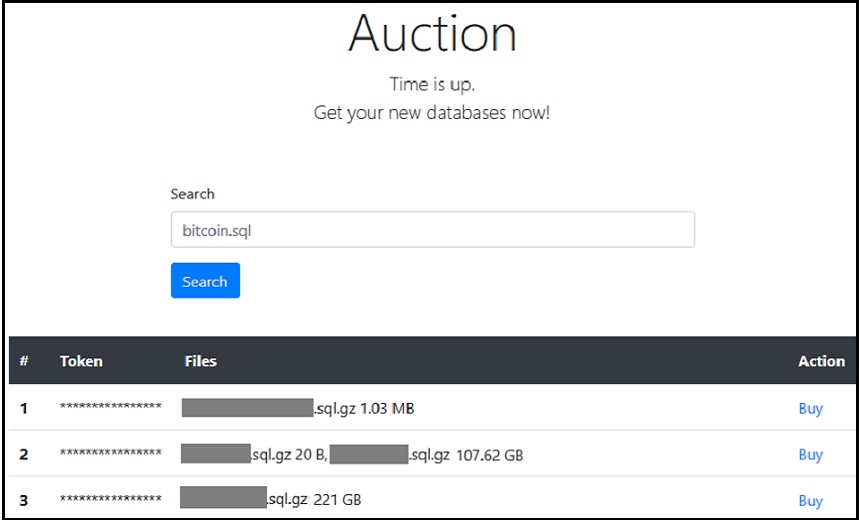
Hackers are targeting thousands of vulnerable MySQL servers around the world, using ransomware to exfiltrate data from organizations as a way to demand payment before making the information public, according to a report released this week by Guardicore Labs.
See Also: The Anatomy of the Solarwinds Attack
In addition to the ransomware and extortion campaign, the hackers are selling access to over 250,000 stolen databases through a darknet market when victims don't pay, according to the report.
The hacking campaign that the Guardicore Labs analysts discovered appears to have started in January and is still active, targeting vulnerable MySQL databases around the world, says Ophir Harpaz, a security researcher, who estimates that about 5 million MySQL servers are exposed to the public internet and are potentially vulnerable to this or another type of attack.
Two Types of Attacks
The attacks happened in two separate phases over the past 12 months.
In the first phase, which started in January and lasted through October, the hackers targeted a vulnerable MySQL server, locked the data with ransomware and then contacted the victimized organization with a ransom note and a bitcoin wallet address to which payment could be sent. The victims were typically given 10 days to pay.
By tracking the activity of the bitcoin wallet used by the hackers, the Guardicore Labs researchers estimate the attackers generated about $25,000 in ill-gotten returns from about 70 separate attackers using this tactic.
By October, however, the hackers changed tactics and started using a double-extortion technique, meaning that data was published as a way to pressure the victims into paying the ransom.
The researchers also note that payment is no longer done directly to the bitcoin wallet, and no email communications are needed. Instead, the attackers put up a website on the anonymous Tor network where payment can be made, and victims are identified using unique alphanumeric tokens they receive in the ransom note.
"The website is a good example of a double extortion mechanism - it contains all leaked databases for which ransom was not paid," according to the report. "The website lists 250k different databases from 83k MySQL servers, with 7 TB of stolen data. Up till now, [Guardicore Global Sensor Network] captured 29 incidents of this variant, originating from 7 different IP addresses."
This shift in tactics has made tracking the attacks more difficult, Harpaz says.
"In the first phase, we could actually monitor bitcoin wallets, and we know for sure that bitcoin was transferred to the attackers' wallets," Harpaz tells Information Security Media Group. "As for the second phase, we cannot monitor the amount of money made as payment is done 'behind the scenes' using the website's user interface. No bitcoin wallet addresses are exposed in this process."
PLEASE_READ_ME
Guardicore Labs named this series of attacks "PLEASE_READ_ME" after a note left on a compromised server. The researchers also note that the type of ransomware used by the hackers is notable for its simplicity and focus.
Unlike other ransomware that tends to move laterally through a network looking for files and data to encrypt, the malicious code used in PLEASE_READ_ME zeroes in on the vulnerable MySQL servers and encrypts the data. To start, the attackers merely attempt to brute-force weak passwords to gain access instead of relying on phishing emails or other means as the initial attack vector, Harpaz says.
"There is no actual malware in this attack, namely, no binary payload executed on the victim machine," Harpaz says. "The attack is based on a simple script which brute-forces database servers, steals data and leaves a ransom note by executing SQL commands. We refer to this campaign as 'malwareless,' because no malware file is practically executed on compromised victims."
The report notes that the attackers do attempt to install a backdoor in the vulnerable MySQL server in case they want to return or maintain persistence.
Attribution?
At this time, the Guardicore Labs analysts cannot attribute these attacks to any particular hacking group. The report notes that most of the attacks originate with IP address based in the U.K. and Ireland.
What also makes these types of attacks successful is that millions of MySQL servers are exposed to the internet and contain weak passwords, Harpaz says.
"Five million MySQL servers around the world are internet-facing," he says. "Databases should not be internet-exposed; they should be protected simply by being internal to the organization's network and accessible only to a limited set of clients. What allows for the PLEASE_READ_ME attack to take place is the fact that countless MySQL servers are internet-facing and that their passwords are easy to guess."





















