COVID-19 , Fraud Management & Cybercrime , Governance & Risk Management
Phishing Email Campaign Uses Updated COVID-19 Theme
Researchers: Fraudsters Offer Lure of $600 Payment for Pandemic Relief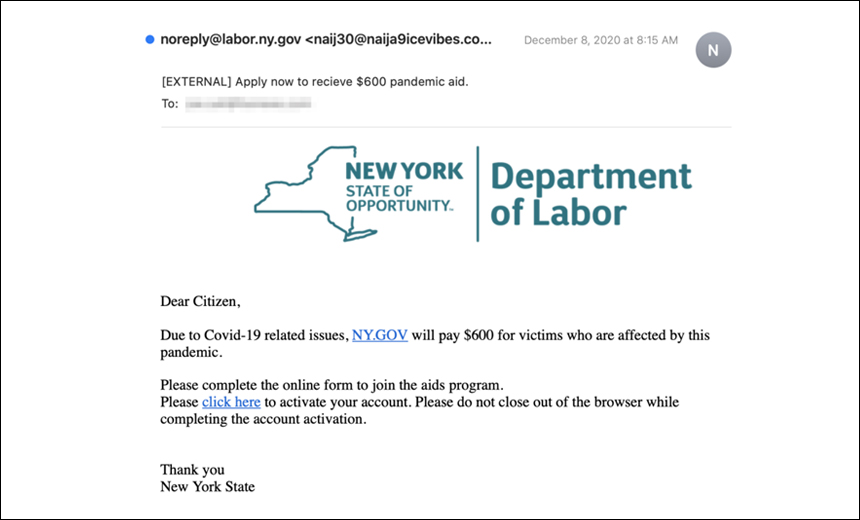
A recently uncovered phishing campaign is spoofing messages from the New York State Department of Labor, claiming to offer $600 as part of a COVID-19 relief program, according to researchers at Abnormal Security. The goal is to harvest personally identifiable information.
See Also: Live Webinar | Social Engineering Campaigns Target You: Don't be a Victim, Be Prepared
This phishing campaign, which appears to have started earlier this month, may have targeted 100,000 Microsoft Office 365 accounts so far, the security firm reports.
"The attackers are taking advantage of the current global health crisis by crafting a scam that revolves around the COVID-19 pandemic and its economic impact," the researchers note. "So, a recipient of this email may be more likely to believe that the government is offering additional relief as the pandemic continues."
The $600 payment mentioned in the phishing emails closely resembles the amount of money that U.S. citizens may start receiving as part of the $900 billion stimulus package passed by Congress on Monday. President Donald Trump, however, has not yet signed the legislation.
"We assume the attackers were matching the amount to increase the sense of legitimacy for the attack because the $600 payments were widely reported prior to passage of the bill this week," says Ken Liao, vice president of cybersecurity strategy at Abnormal Security.
Phishing Emails Promise Relief
The phishing emails are sent using an email address that displays as "noreply@labor.ny.gov" and the messages display a New York state government logo at the top of the email. The true sender, however, is "naij30@naija9icevibes.com," a Panamanian-registered domain, according to the report.
The fraudsters’ message claims that the Labor Department is offering a $600 relief fund payment if they fill out a form, which is an embedded link within the phishing email. After clicking the link that is supposed to lead to an official state government site, the potential victims are actually taken to a phishing landing page - https://thesender[.]org/fjc4 - where their personally identifiable information is harvested, including name, address, date of birth, Social Security number and driver’s license number, according to the report.
Other Spoofing Attacks
Since the onset of the COVID-19 pandemic, fraudsters have been using pandemic themes in phishing campaigns.
In early December, for example, Russia-linked hackers were seen using phishing emails with COVID-19 themes as a way to infect devices with a backdoor called Zebrocy, the security firm Intezer reports (see: Phishing Emails With COVID-19 Themes Delivered Zebrocy Malware).
In July, the FBI warned that the operators behind Netwalker were using COVID-19 themes as a lure to entice victims to open phishing emails that contained malicious attachments (see: FBI: COVID-19-Themed Phishing Spreads Netwalker Ransomware).
Also, the FBI identified nearly 100 spoofed websites in November that use some incarnation of the agency's name. Fraudsters and other cybercriminals could potentially leverage these for disinformation campaigns and credential theft (see: Fraudsters Spoof FBI Domain).
"Heading into the holiday season, these bad actors are poised once again to convert news surrounding the development and distribution of COVID-19 vaccines into a powerful tool for social engineering your users and employees through phishing campaigns that exploit their very real questions and concerns about the vaccine," Eric Howes, principal lab researcher at security firm KnowBe4, notes in a recent blog post.





















