Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development
Iranian Hacking Group Again Targets Universities
Malwarebytes: 'Silent Librarian' Seeks Intellectual Property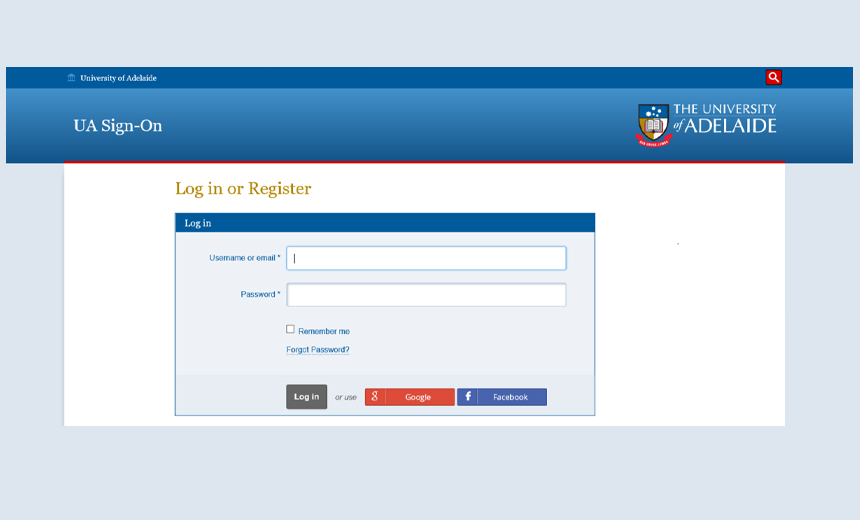
A hacking group with suspected ties to Iran's government is again targeting universities in the U.S. and around the world, according to researchers with security firm Malwarebytes.
See Also: Enabling Government for Modernized IT
“Silent Librarian," which is also referred to as TA407 and Cobalt Dickens, targets academic institutions to steal intellectual property and research documents. The hacking group's activities, which began in 2013, usually start in September to coincide with the new school year, according to the report (see: 'Silent Librarian' Revamps Phishing Campaign: Proofpoint).
Because many schools and universities are offering virtual classes this fall, the hacking group has revamped its phishing emails and other techniques to target remote students and university staffers, the Malwarebytes report notes.
"Another school year, and yet again we see Silent Librarian busy sending out phishing emails and deploying phishing sites," the Malwarebytes researchers note. "However, this year is different with more students and teachers being remote. This could open up new opportunities for the attackers in crafting convincing emails and luring in more victims."
The Malwarebytes report notes the group has targeted over a dozen universities since it resumed its operations in September. Those include the University of Oxford in Britain, Australia's Catholic University and Nanyang Technological University in Singapore, according to Peter Kruse, who heads the eCrime Unit at CSIS Security Group in Denmark and has been tracking the group's activities over the last week.
Today Iranian APT Silent Librarian (aka Cobalt Dickens or TA407) is attacking Nanyang Technological University in Singapore: https://t.co/F701O9oA5m[.]https://t.co/f3xtxAdzGZ @CSAsingapore @douglasmun pic.twitter.com/wdxHu6Nhz4
— peterkruse (@peterkruse) October 13, 2020
Connections to Iran
Silent Librarian's activities have been sanctioned by the Iranian government to raise money for the regime as well as to support its development in the fields of science and technology, according to Malwarebytes.
"Considering that Iran is dealing with constant sanctions, it strives to keep up with world developments in various fields, including that of technology. As such, these attacks represent a national interest and are well funded," according to the report.
In March 2018, the U.S. Justice Department unsealed an indictment against the group, which federal prosecutors called the Mabna Institute, alleging that its members had targeted universities across the U.S. for several years
The federal indictment included charges of computer intrusion, wire fraud and identity theft. The indictment also noted that the hacking group is allegedly tied to Iran's Islamic Revolutionary Guard Corps, a paramilitary group that's also involved in cyberespionage.
Targeting Universities
The latest Silent Librarian campaign builds on its previous tactics, starting with sending out phishing emails that use logos and artwork from schools, according to the report.
The phishing emails typically contain a link that leads to what appears to be a university sign-in portal webpage. The sites, however, are phishing domains controlled by the hacking group that are designed to harvest credentials, according to the report.
The Silent Librarian group uses Cloudflare to hide the phishing pages' real hosting site. Some of this infrastructure is now hosted in Iran, which is a change from past campaigns, according to the researchers.
"It may seem odd for an attacker to use infrastructure in their own country, possibly pointing a finger at them," the report states. "However, here it simply becomes another bulletproof hosting option based on the lack of cooperation between U.S. or European law enforcement and local police in Iran."
Prolific Hacking
The hacking group has targeted over 140 organizations in the U.S. and 170 universities and schools in 21 other countries around the world since 2013, according to a report published last year by Proofpoint.
From 2013 to 2017, the hackers stole over 30 terabytes of data, Proofpoint reported.






















