Fraud Management & Cybercrime , Governance & Risk Management , Privacy
Instagram Leaked Minors' PII Again, But Now It's Fixed
Exposure Comes as Ireland Probes Facebook's Handling of Children's Data
For at least a month, Instagram leaked the email addresses of minors, which occurred as Ireland’s Data Protection Commission probed whether Facebook failed to protect children’s personal data.
See Also: Managing Digital Risk and Compliance in Financial Services
Facebook has fixed the issue, which was brought to its attention on Oct. 19 by David Stier, a San Francisco-based data scientist.
It’s the second time Facebook has fixed this kind of error in Instagram, raising questions over how carefully the company protects personal data.
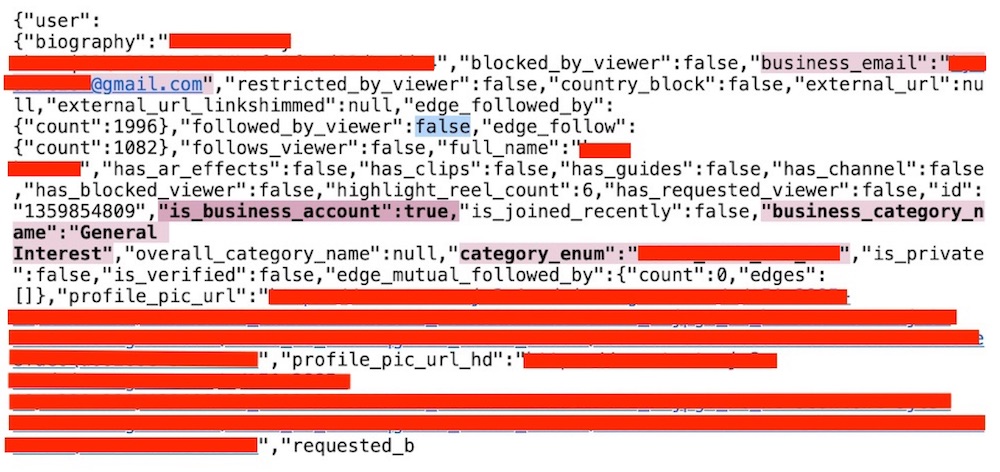
Stier found that Instagram was exposing minors’ email addresses within the HTML source code for Instagram profiles viewed through a web browser rather than the app. The email addresses belonged to minors who had converted their personal profiles to business profiles.
The email addresses, Stier contends, could be easily scraped. That doesn’t meet the standard of care that companies should adhere to, particularly as it affects minors, Stier says.
“The concern is that these [email addresses] are displayed in the source code of every page and are part of the structured data layout,” Stier says.
Stier emailed Stephen Deadman, who is Facebook’s vice president of data protection and leadership in London, showing the exposed email address of a young teenage girl from Illinois.
Businesses Without Businesses
Millions of minors who don’t have legitimate businesses have converted their profiles to business profiles. Business profiles have enhanced analytics tools that show how posts perform, which is a reason kids may have opted to convert their profiles.
Instagram used to require that those who have business profiles provide their email addresses or phone numbers. Also, by default, all content on a business profile is public.
As a result, Stier found in early 2019 that the email addresses and/or phone numbers of millions of minors had been exposed. Child safety experts said that Facebook was needlessly exposing contact details, which could potentially make it easy for strangers to contact children online (see: Instagram Shows Kids' Contact Details in Plain Sight).

Stier filed a complaint with Ireland's Data Protection Commission, which regulates Facebook in Europe and enforces the General Data Protection Regulation and the Data Protection Act of 2018.
In September 2019, Facebook added settings that allowed people to keep their email address and phone number private even if they use a business profile on Instagram. Nonetheless, after a year of consideration, the Data Protection Commission announced an investigation last month (see: Instagram Investigated for Exposure of Minors' Details).
Although kids can now choose whether to expose their email addresses and phone numbers, the DPC’s investigation is looking at whether Instagram’s account settings are appropriate for children. A second line of inquiry is looking at Facebook’s legal basis for processing children’s data and whether it uses adequate protections for children.
Facebook has said that Stier’s findings mischaracterize what the DPC is investigating, saying it had been clear to users that business profile data would be made public and that Facebook had made changes to allow users to opt out of sharing contact data.
It’s not clear how many children take advantage of the new settings to better protect their privacy.
Same Error Twice
Stier’s latest finding mirrors one to which he alerted Facebook in February 2019. At that time, he found kids’ email addresses and phone numbers within the HTML source code in the web version of Instagram profiles.
Facebook, Stier says, “immediately fixed it as soon as it was brought to their attention.”
This time around, only email addresses were in the HTML source code, and they were only exposed if a minor had opted to show that information publicly in the app as well, he says.
Stier says it’s easy for someone with bad intent to begin scraping the data. Most online services use technical safeguards to ward off scraping, which is against Instagram’s terms of service.
But scraping is difficult to stop, particularly when it’s done in a fashion that closely mimics real user activity. While doing his research, Stier says, he was able to view and download the source code for more than 25,000 Instagram profiles a day and didn’t run into any limits.
By default, photos and data in a business profile are public. So, Stier says, once someone finds a minor’s profile, the child’s profile photo, bio and photos can be collected. Kids often write their school year or hint at their age in profiles, making the process of sorting out who is a minor easier.
“Once you have just 100 names of identified kids, then you can easily scrape a list of all of their followers and then use that to go scrape those web pages,” Stier says. “Soon, you’d end up having a very substantial number of email addresses.”
Facebook’s Explanation
The reintroduction of PII into the HTML source code apparently came about as part of Facebook’s efforts to allow people to mask their contact information despite having a business profile.
Facebook added a toggle setting in September 2019 that allows people to hide their contact information on a business profile. On Friday, Facebook Ireland told Stier that, to have the capability in the web version of Instagram to toggle off contact data, the email address had to be included in the HTML.
If users chose to hide their contact data, the email address would be removed from the HTML, Facebook said.
Facebook tells Stier it considered the issues he raised and decided to find a way to provide the same functionality to users “without including email addresses in the HTML of a page in this way.”
Sometime after Nov. 14, Facebook made the change. Facebook officials did not immediately reply to a request for further comment.
Stier says that, after Facebook makes code changes, it should routinely check to ensure that no personally identifiable information is leaked.
“This most recent leak of PII demonstrates that Instagram appears unable to implement the simplest of data protection practices,” he says.