Blockchain & Cryptocurrency , Cybercrime , Endpoint Security
Cryptojackers Keep Hacking Unpatched MikroTik Routers
Vigilante Hacker Is Killing Unpatched Routers' Remote Administration Ability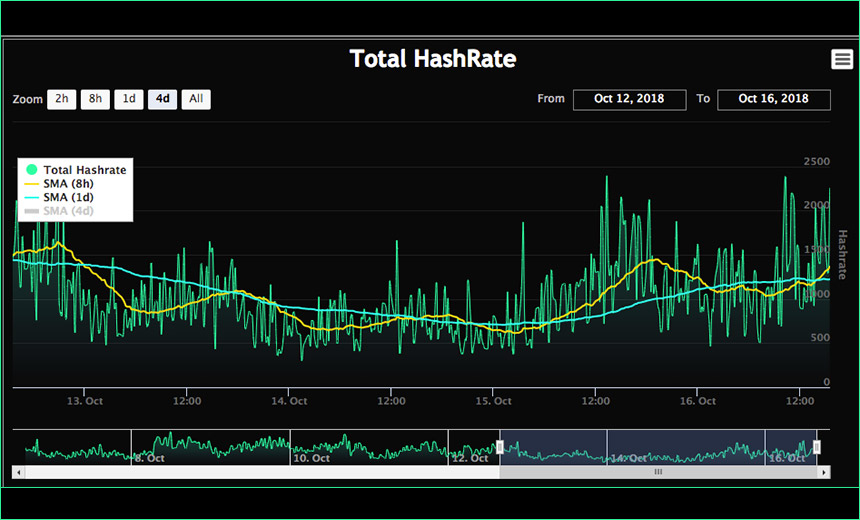
Attackers are continuing to compromise unpatched routers, as well as devices with default credentials, built by Latvian manufacturer MikroTik.
See Also: What GDPR Means for Cybersecurity
More than 2 million MikroTik routers appear to be internet-connected. Of those, security experts say that more than 420,000 appear to have been exploited and infected with malicious cryptocurrency-mining scripts (see Hacked MicroTik Routers Serve Cryptocurrency-Mining Malware).
In April, MikroTik rapidly patched a zero-day flaw, designated CVE-2018-14847. Via the flaw, attackers can gain complete access to a vulnerable router, giving them access to Winbox - a simple GUI administration utility for MicroTik's RouterOS - as well as Webfig - the web-based version of the utility.
Since then, despite clear and persistent warnings from security researchers as well as MikroTik, hundreds of thousands of its routers remain unpatched and are being actively targeted by attackers, security researchers say.
On Tuesday, Ankit Anubhav, principal security researcher at New Sky Security, said that a new honeypot it launched to study how the MikroTik router flaw is being exploited found that it's largely being targeted by already infected MikroTik routers.
So our #mikrotik honeypots are functioning now, and the first attack IPs trying to attack us are themselves infected mikrotik devices. (same coinhive key)
— Ankit Anubhav (@ankit_anubhav) October 16, 2018
In case you are infected, your device is probably not only mining for the attackers but also trying to infect other mikrotik https://t.co/aM8YGNTb5z
Security researchers Martin Hron and David Jursa at Czech security vendor Avast say at least several strains of MikroTik-infecting malware appear to be in play, noting that Avast found and disrupted a command-and-control network associated with at least two domains. But they say whoever was behind the attacks quickly retrenched.
"Just shortly after we took down the second domain, the attacker started to tighten-up the compromised devices, by disabling most of the management interface, and moving ports of SSH and telnet to port TCP/10022 and TCP/10023, which is unexpected and incredibly unlikely that a user would even notice," Hron and Jursa say in a blog post. "The attacker continued to tighten up his position in the router. For example, it's now almost impossible to connect to the telnet port; once you connect using leaked credentials, the router disconnects you almost immediately."
Avast says that from Sept. 19 to Oct. 15, it blocked "blocked malicious cryptomining URLs related to infected networks with MikroTik gateways, also known as the WinBox vulnerability, over 22.4 million times."
Those blocks will have involved only endpoints running Avast's software, so the statistics don't offer a complete look at how many attacks infected MikroTik routers might launching worldwide. But even the tranche of attacks seen - and blocked - by Avast is significant.
Avast says that the CVE-2018-14847 flaw likely isn't the only way that attackers have been exploiting MikroTik devices. "We believe the routers could also have been exploited because their owners didn't change their default credentials or created weak passwords," the researchers say.
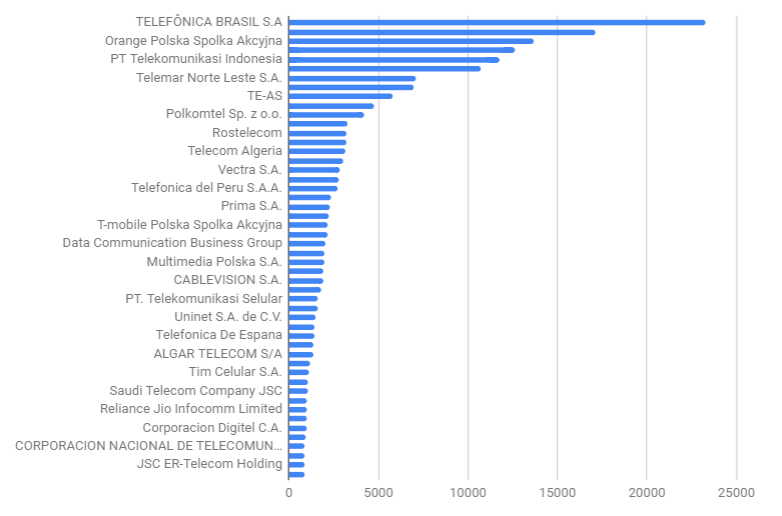
Indeed, Avast says that it counts about 314,000 MikroTik routers across its user base. And it says its researchers have found that "85.5 percent are vulnerable to the Winbox exploit," due primarily to only about 5 percent of the devices having been updated with the latest MikroTik firmware, which fixes CVE-2018-14847.
Proof-of-Concept Exploit Writes Files
Interest in the flaw has continued to intensify since April. Earlier this month, researchers at Tenable released By the Way, a proof-of-concept exploit that demonstrates how CVE-2018-14847 and other flaws that they discovered can be abused to not only take full control of a vulnerable MikroTik device running RouterOS but also to write arbitrary files to the device.
"Post-exploitation, the attacker can connect to telnet or SSH" on the device by "using the root user 'devel' with the admin's password," the researchers say in a blog post.
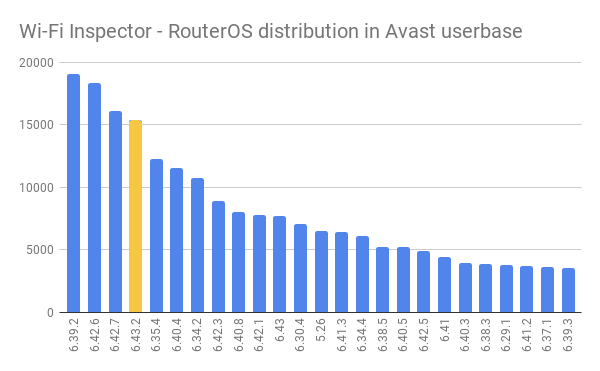
Those flaws have been fixed in RouterOS by MikroTik, via the introduction of RouterOS versions 6.40.9, 6.42.7 and 6.43.
Follows VPN Filter Alert
Cryptojackers are not the only attackers to have been targeting MikroTik routers.
In May, the FBI warned that it helped to interrupt an attack campaign that had infected 500,000 MikroTik routers with "VPN Filter" malware, in what appeared to be preparation for launching a major attack. Instead, however, the FBI was able to sinkhole the malware, disrupting the botnet controllers' ability to send instructions to infected devices. The bureau attributed the attack to a hacking group run by Russia's military intelligence bureau, the GRU, that is also known as Fancy Bear, as well as APT28, Pawn Storm, Sandworm, Sednit, Sofacy, Tsar Team and x-agent (see Chaos on the Cheap: 'Fancy Bear' Malware Weaponizes Routers).
"VPNFilter reportedly targets default credentials, the standard usernames and passwords enabled on the device out of the box, which users often leave unchanged," the Tenable security researchers say in their blog post. "The actual vulnerabilities being used by VPNFilter are not fully known."
But they note the targeted bugs may have included the ones that they discovered and have exploited via their By the Way exploit.
Hackers Cryptomine, Eavesdrop
Last month, researchers at 360's Network Security Research Lab warned that attackers had been eavesdropping on more than 7,500 MikroTik routers, while also using another 239,000 compromised routers to serve as proxies (see MikroTik Routers Targeted in Data Eavesdropping Scheme).
That followed Troy Mursch of Bad Packets Report in August warning that more than 209,000 carrier-grade MicroTik routers had been infected with one of two different types of software - Coinhive and Crypto-Loot - that mine for cryptocurrency. Both are small JavaScript programs that mine for monero.
United States ISPs with compromised #MikroTik routers injecting Coinhive.
— Bad Packets Report (@bad_packets) October 13, 2018
Censys query: https://t.co/4fZ9jOUfMW pic.twitter.com/DvRwWh4EfN
On Oct. 12, Mursch found more than 6,700 MikroTik routers connected tied to U.S. internet service providers had been hacked and were being used to mine for cryptocurrency via Coinhive.
Configuration File Needs Cleaning
Preventing MikroTik routers from getting popped via CVE-2018-14847 requires updating to the latest firmware.
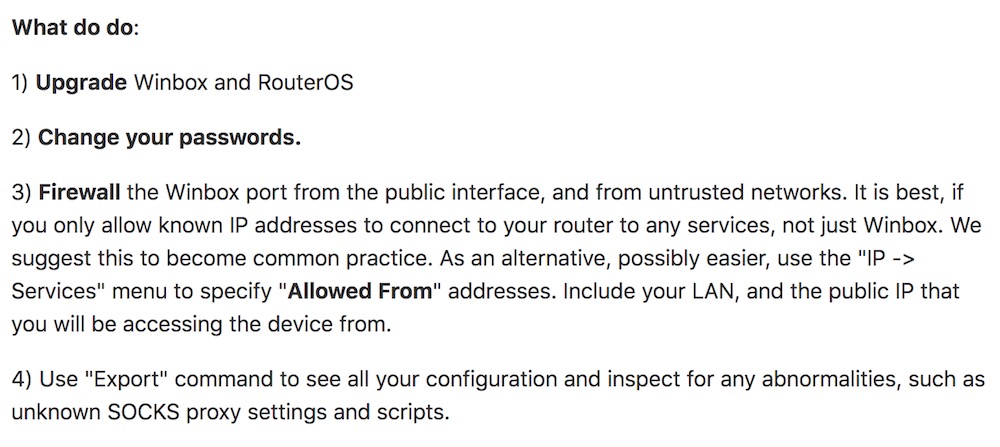
For any device that's already been exploited, however, the administrator must also replace a malicious configuration file that will have been placed by attackers.
Remediation has to be done for each infected device. Simply updating to the latest RouterOS doesn't fix the problem. https://t.co/xEqGbd4sgq
— Bad Packets Report (@bad_packets) October 15, 2018
Unfortunately, many users never update device firmware (see War Declared on Default Passwords).
Enter Vigilante Hacker
Last week, a Russian "gray hat" hacker named Alexey embarked on a vigilante campaign to forcibly patch vulnerable MikroTik routers by removing their remote administration ability, ZDNet reported.
Alexey claimed to have cleaned more than 100,000 devices, and said he left his Telegram account information on all of the systems for anyone who cared to comment. Alexey told ZDNet that only about 50 people ever contacted him, with a few saying thanks, while the rest expressed outrage.
Jake Williams, a former member of the National Security Agency's hacking team who's now head of consultancy Rendition InfoSec in Augusta, Georgia, said there were discussions after the EternalBlue flaw was found about whether "good guy" hackers should patch all vulnerable systems (see Eternally Blue? Scanner Finds EternalBlue Still Widespread).
In theory, doing so would protect not only the organizations that rely on those devices, but everyone else as well, because hackers would no longer be able to exploit the vulnerable systems and networks to launch attacks against others.
The same can be said now for so many MikroTik routers.
"As you look around these routers, they're obviously vulnerable," Williams says in a video posted to YouTube. "Absent a vigilante doing this, nobody else is going to patch these routers."
Hacking a Router to Install a Security Update: Ethical?
But an intrusion is an intrusion, Williams warns, and can have many unintended effects, including knocking an organization's internet access offline. "Regardless of intent, a crime is a crime, and the attacker shouldn't be doing this," he says. "We're talking about whole networks just dropping offline. ... Those remote-admin ports may have been enabled for a reason."






















