Cybercrime , Cybercrime as-a-service , Endpoint Security
Darkside Ransomware Gang Launches Affiliate Program
Using Affiliates Enables Crowdsourced Profits But Leaves Operators More Exposed
Darkside is the latest ransomware gang to announce that it's launched an affiliate program as part of its bid to maximize revenue.
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
In recent days, the operators behind Darkside have taken to XSS and Exploit - two major, Russian-language cybercrime forums - to announce the details of the gang's new affiliate program, Israeli cyberthreat intelligence monitoring firm Kela reports.
Here's how such affiliate programs work: Ransomware operators provide crypto-locking malware code to third parties. Each affiliate receives a version of code with their unique ID embedded. For every victim that pays a ransom, the affiliate shares the take with the ransomware operator.
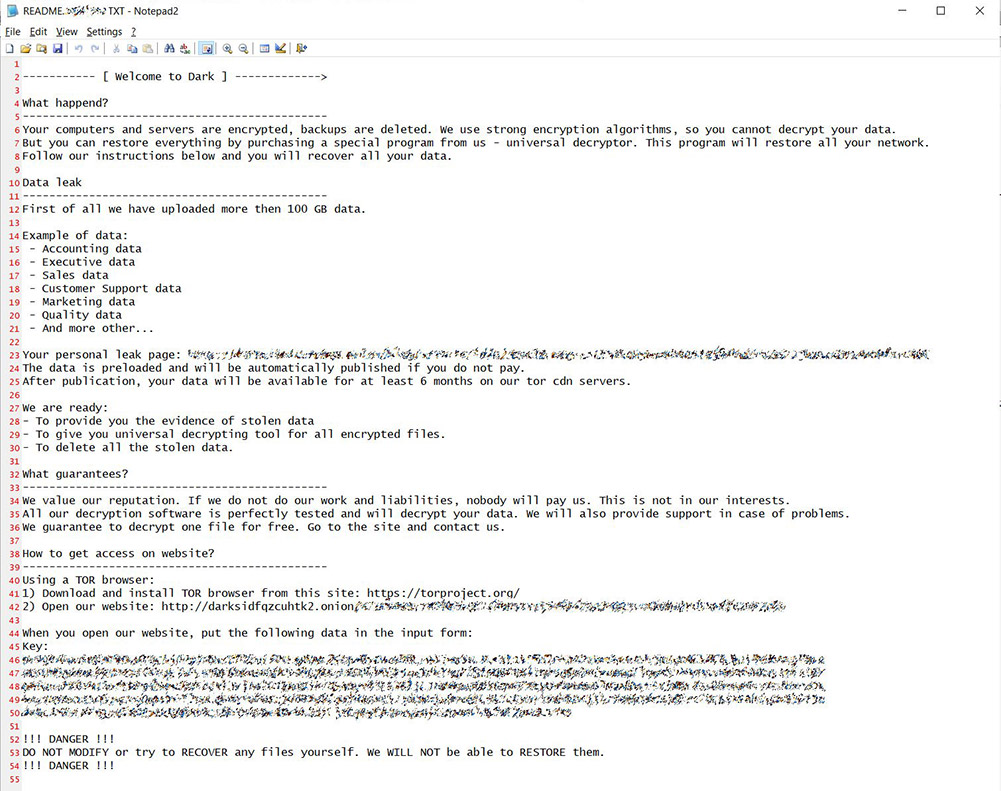
For example, the affiliate program run by Sodinokibi - aka REvil - as of last year was giving 30% of every ransom payment to an affiliate, rising to 40% after three successful ransom payments (see: Sodinokibi Ransomware Gang Appears to Be Making a Killing).
Darkside's terms and conditions differ. "They stated that their average payments to their affiliates are about $400,000 and the share paid to affiliates is about 75-90% of every haul, depending on the size of the ransom, with the ransomware operators keeping the remainder," Kela says, noting that Darkside claims the average ransom it receives is between $1.6 million and $4 million.
Ransomware affiliate programs abound. Victoria Kivilevich, a threat intelligence analyst at Kela, says some of the more famous "big game" ransomware operators running affiliate programs - as well as blogs for leaking stolen data - include:
- Avaddon;
- Darkside;
- LockBit;
- Netwalker;
- Ranzy;
- Sodinokibi, aka REvil;
- Suncrypt - now apparently retired.
Other ransomware operations - some active, some now defunct - that have run affiliate programs include Chimera, CryLock, Exorcist, Gretta, Makop, Thanos and Zeppelin, she says.
Affiliate Program Upsides
Running an affiliate program offers numerous upsides. For starters, the ransomware operator handles the technical side, including "product updates." Once the operator has built all required infrastructure - typically including a self-service portal for victims to pay - they can, in theory, scale to handle as many affiliates as they want. This crowdsourcing model can give them the ability to realize much greater profits, especially compared to trying to hit victims themselves. Affiliates, meanwhile, don't need to build and maintain their own malware and infrastructure.
Other upsides include the ability of the operation to attract specialists - in network penetration, for example - who can focus on amassing victims while leaving tech support and customer service, so to speak, to the operator.
Two Main Downsides
So, what are the downsides to running an affiliate program? Kivilevich highlights two main problems: reputation and infiltration.
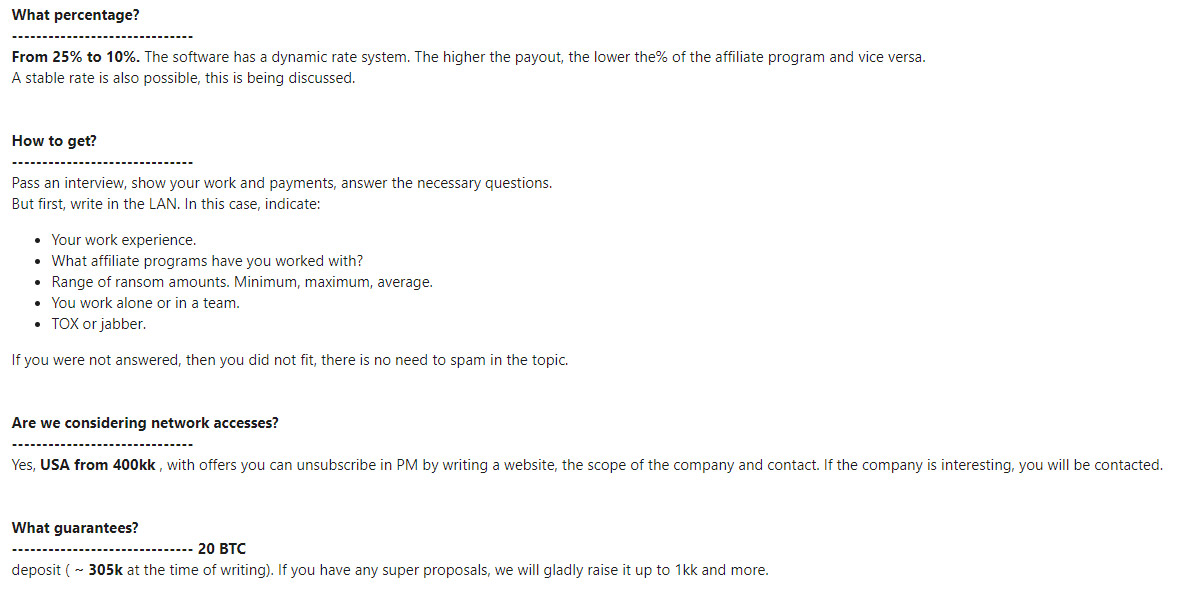
If an affiliate does something bad, that reflects on the operator, as Darkside has noted in one of its posts. "For example, when an affiliate of Suncrypt attacked hospitals, you see Suncrypt writing: 'A new affiliate locked it unknowingly, and for this he was punished! Hospitals, government, airports, etc., we do not attack,'" she says.
Relying on affiliates also means that the ransomware operation may be inadvertently recruiting undercover security researchers or law enforcement agents who might potentially "gather more intelligence about their activities," Kivilevich says.
Ransomware Features
How big a threat does Darkside pose? The operators say that the crypto-locking malware that Darkside provides to affiliates can encrypt both Windows and Linux files. Researchers at Russian security firm Kaspersky recently determined that RansomEXX ransomware also can crypto-lock Linux files (see: RansomEXX Ransomware Can Now Target Linux Systems).
Like many types of malware, Darkside is designed so it cannot infect PCs that are in one of the member states of the post-Soviet Commonwealth of Independent States, which includes Russia and 11 other nations (see: Russia's Cybercrime Rule Reminder: Never Hack Russians).
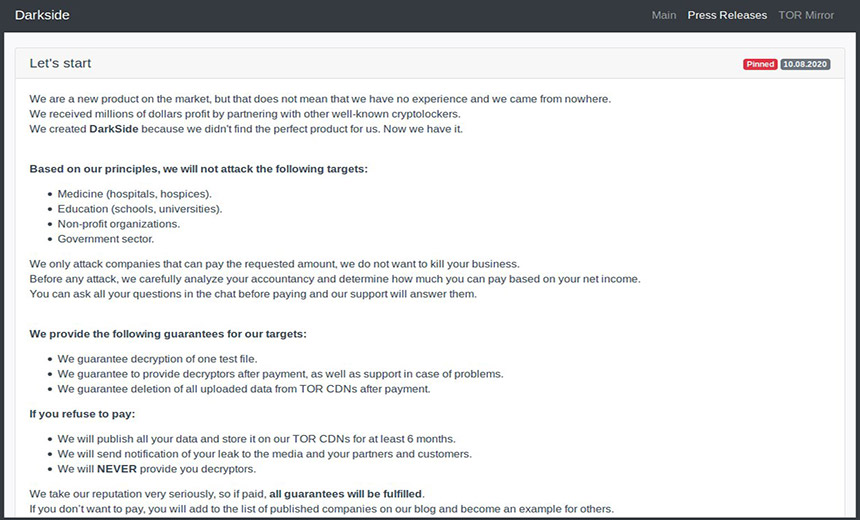
As proof of its success to date, Darkside has deposited 20 bitcoins - worth about $315,000 - with the XSS forum. Kivilevich says this is "a common method ransomware gangs will use to show that their operation generates plenty of profit."
Like many other ransomware operations, the gang maintains a leak site, where it names and shames victims and can post samples of stolen data to try to force victims to pay (see: Data-Exfiltrating Ransomware Gangs Pedal False Promises).
Even so, it's not yet clear how many organizations Darkside or its affiliates might have hit.
"Darkside has been relatively quiet since the gang emerged. They've published only four victims on their site, with one being removed," Kivilevich says. "It's possible the gang is extending their efforts, meaning that we could expect to see them performing more attacks."
In a likely bid to boost profits, the gang has posted that it's looking for initial access brokers that can give it access to U.S. businesses with annual revenue of at least $400 million.
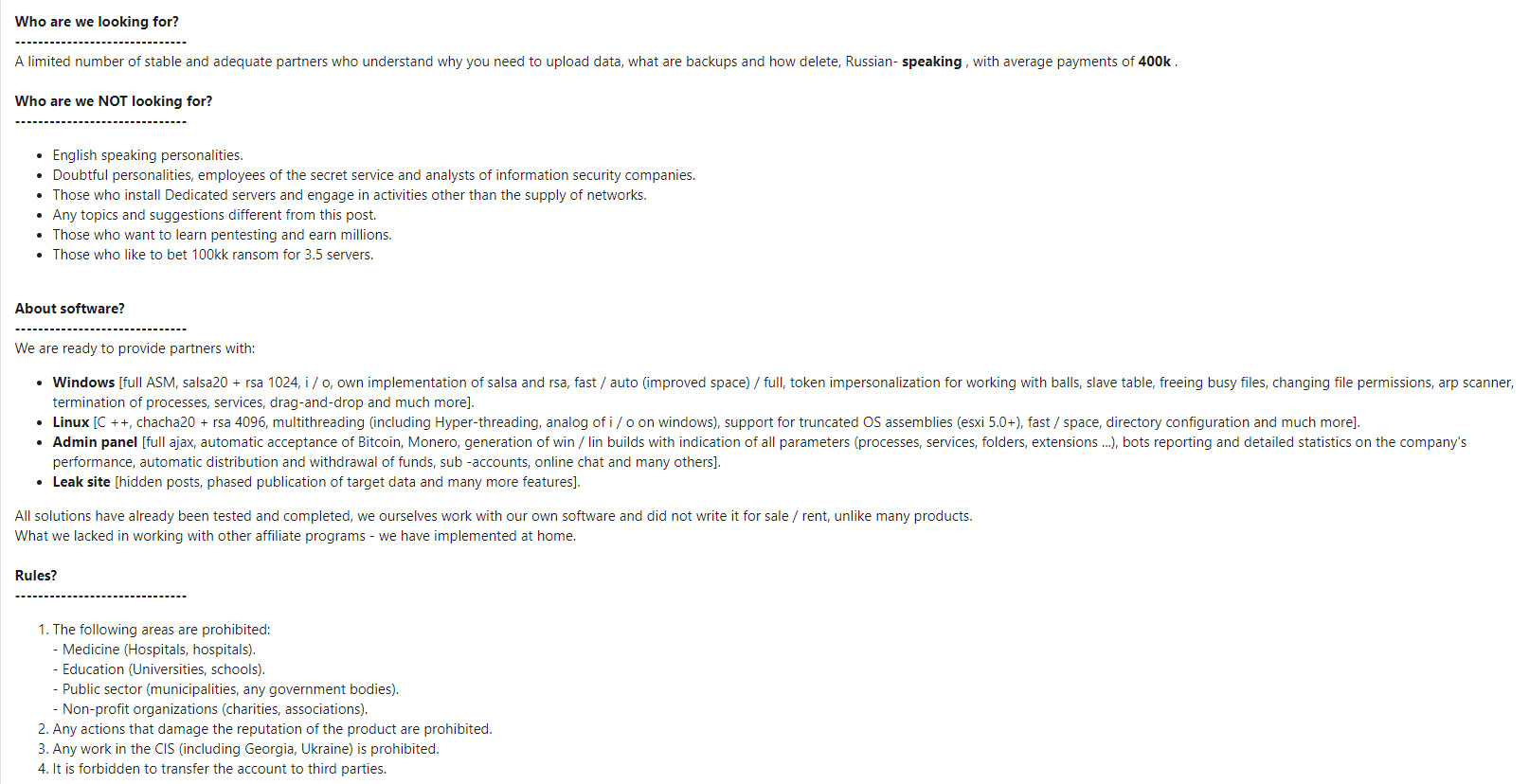
"Darkside is aiming for big targets," Kivilevich says, adding that it's the first time she's seen "ransomware operators offering initial access brokers the opportunity to directly trade with them" rather than attempting to rely on "affiliates or other middlemen."
As always with ransomware, criminal innovation - in a nonstop drive by attackers to maximize profits - appears to be paying off at victims' expense.
This piece has been updated to clarify the amount DarkSide pays to affiliates.











