Cybercrime , Cybercrime as-a-service , Fraud Management & Cybercrime
4 Bulletproof Hosting Provider Admins Getting Sentenced
Bulletproof Hosting Service Supported Zeus, SpyEye and Citadel Malware, Says FBI
How did criminals bring such banking Trojans as Zeus, SpyEye and Citadel, as well as attack tools such as the Blackhole exploit kit, to bear on victims?
See Also: Take Inventory of Your Medical Device Security Risks
Many were users of a bulletproof hosting service that U.S. authorities say was run in part by four men from Eastern Europe and helped criminals to facilitate numerous malware, botnet and other online-attack schemes, including issuing large quantities of malware-laden spam.
Bulletproof hosting refers to infrastructure that gets provided to criminals to help them launch online attacks. Typically, bulletproof hosting servers are run by administrators who ask few questions and who won't respond to takedown requests or court orders - for example, if a foreign internet service provider or law enforcement agency traces malware attacks, botnet hosting or spam to the service's servers or requests evidence for building a case.
The hosting service that is the focus of this case has not been named by authorities or in court documents.
All four suspects were extradited last year from Eastern Europe to stand trial in the U.S. Authorities say additional suspects "known and unknown" who were part of the operation remain at large.
Sentencing Underway
Two of the men - Pavel Stassi, 30, of Estonia, and Aleksandr Skorodumov, 33, of Lithuania - have respectively been sentenced to serve two years and four years in prison by Chief Judge Denise Page Hood of the U.S. District Court for the Eastern District of Michigan, the U.S. Department of Justice says.
Both reached plea agreements with prosecutors earlier this year and agreed to plead guilty to one count of Racketeer Influenced and Corrupt Organizations Act, or RICO, conspiracy, which carries a sentence of up to 20 years in prison.
Stassi was sentenced on June 28, and Skorodumov was sentenced on Wednesday.
Two co-defendants, Aleksandr Grichishkin and Andrei Skvortsov, both 34 and Russian nationals, also pleaded guilty to one count of RICO conspiracy. Sentencing for all of the defendants was originally scheduled to have concluded by September, but has been delayed, no doubt due in no small part to slowdowns caused by the ongoing COVID-19 pandemic.
The indictment charged all four men not just with the one RICO count, but also with one count of bank fraud conspiracy, which appears to have been dropped.
"Over the course of many years, the defendants facilitated the transnational criminal activity of a vast network of cybercriminals throughout the world by providing them a safe haven to anonymize their criminal activity," says Special Agent in Charge Timothy Waters of the FBI's Detroit Field Office. "This resulted in millions of dollars of losses to U.S. victims."
Roles and Responsibilities
The two Russians - Grichishkin and Skvortsov - launched the service and served as its proprietors, with the former acting as the "day-to-day leader," according to a superseding indictment against the four men filed in February 2020 and unsealed on March 4, 2020.
According to court documents:
- Grichishkin "oversaw advertising on online forums, set pricing for hosting services, negotiated and interfaced with clients, managed employee hiring and compensation, and supervised the systems administrators' and other employees' work."
- Skvortsov "served as a reference for the organization on online cybercrime forums, where businesses' success depended upon reputations and relationships." He also referred clients and helped refine the business and resolve any problems encountered by customers - especially VIPs.
- Skorodumov, the Lithuanian, served as a system administrator from at least December 2009 until May 2012.
- The Estonian, Stassi, "performed client relations and administrative services" from at least November 2010 through September 2014, and also helped Grichishkin screen orders, support customers and provide technical support.
The administrators employed fake or stolen identities to register the infrastructure they used and create PayPal accounts for funding the services, to better evade law enforcement detection, authorities say.
Customer Service for Malware Operators
The administrators also monitored "sites used to blocklist technical infrastructure used for crime," such as Spamhaus and ZeusTracker, and move any "flagged" content to a different part of their infrastructure to keep it online, authorities say.
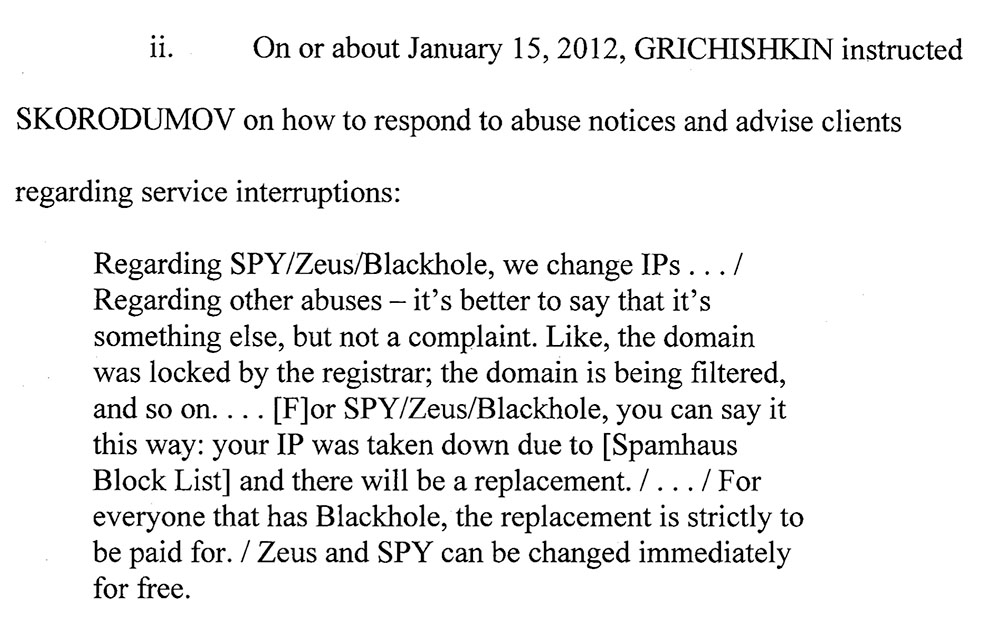
The bulletproof hosting service also advertised "free, within reason," 24-hour support to customers via ICQ and Jabber, according to court records.
The group allegedly also worked to build ties with cornerstones of the cybercrime-as-a-service ecosystem. For example, in April 2010, "at Skvortsov's direction, Grichishkin contacted the developer of the SpyEye banking Trojan, 'offer[ing] to collaborate' and proposing 'you can refer clients to us and I will payout a fixed amount for each one,'" according to court documents.
Security experts say SpyEye was the dominant malware toolkit cybercriminals used from 2009 to 2011 (see: Two SpyEye Malware Masterminds Sentenced).
Blast From the Cybercrime Past
The historical nature of the case is highlighted by some of the malware and banking Trojans the defendants helped support, as well as facilitating the use of the Blackhole exploit kit, all of which have seen a sharp decline in use in recent years.
Exploit kits are automated attack tools that identify vulnerabilities in a user's system - typically in their browser - and then exploit those flaws to install malware. Malicious links, legitimate websites that have been subverted and malicious attachments are all regular ways such toolkits are used to attack users.
But the use of exploit kits has declined significantly since their heyday in the early 2010s, due in no small part to developers of the most targeted software - including Microsoft's Internet Explorer browser and Adobe's Flash and PDF plug-ins - adding automatic updating capabilities to their software and forcibly deleting outdated versions. Those and other measures have helped reduce the attack surface once posed by the outdated and vulnerable software being run on millions of PCs.
Where malware attacks are concerned, meanwhile, banking Trojans were largely supplanted by crypto-locking malware and then cryptocurrency-mining malware. More recently, ransomware has regained popularity, although miners still remain popular (see: Is Cryptocurrency-Mining Malware Due for a Comeback?).
Building Cases Takes Time
In other words, this case has taken a considerable length of time to build, as has bringing the suspects to justice. In particular, the men stand accused of crimes they committed from August 2008 until at least November 2015.
But authorities say long time frames are not unusual for building cybercrime cases, which can be complex and lengthy undertakings, and even more so if they're international in scope. This case, for example, was investigated by the FBI, backed by law enforcement agencies in Germany, Estonia and the United Kingdom.
"Given their international nature, and the anonymity of the internet, cybercrime investigations often take years," says Saima Mohsin, the acting U.S. attorney for the Eastern District of Michigan. "They require the resources of multiple law enforcement agencies, the cooperation of multiple governments, skilled interpreters, and time-consuming extradition procedures."